Appearance and dimensions
The overall dimensions of the machine are: 9.5″ (W) x 12.75″ (H) x 11″ (D), or 24.1cm x 32.4cm x 27.9cm.
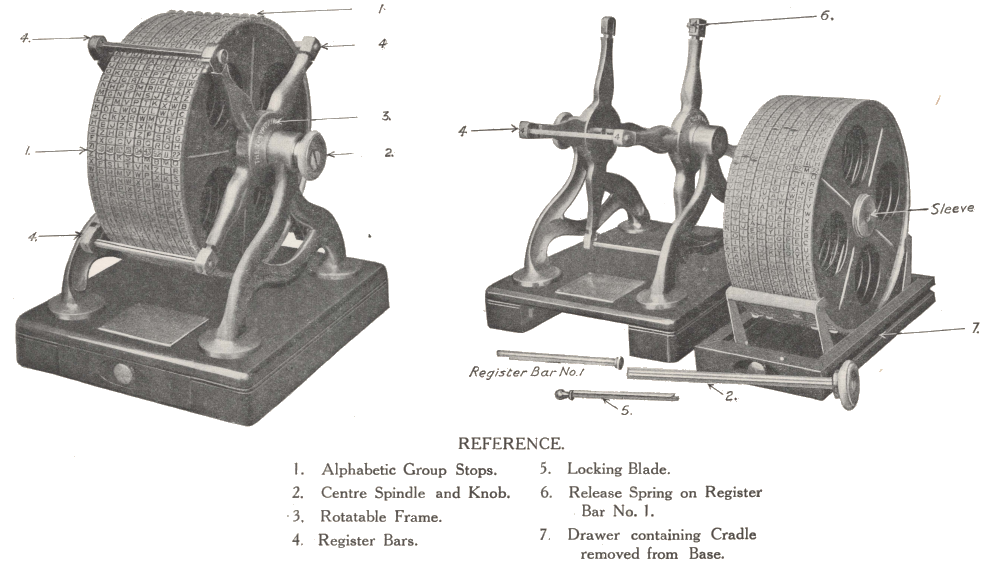
The device consists of:
- 10 bronze-edge discs with spokes. They each have 4 alphabets stamped around the rim, separated by the alphabet number and a stop. Vowels and the alphabet numbers are red, consonants are black.
- A spindle around which the discs and arms rotate.
- A knob.
- 4 quadrant arms stemming on each side of the discs. They can rotate around the spindle, and their ends can be depressed so the register bars they hold prevent the discs from rotating beyond the stops separating the alphabets.
- 4 numbered register bars. They prevent full rotation of the discs when the quadrant arms’ sleeves are depressed, and are used as markers to read or build up the plain or cipher text.
- A support frame.
- A beech base with a drawer. The drawer shows an instruction sheet, and can be removed from the base and used as a cradle for the discs when reordering them.
Alphabets
A unique feature of the Cryptocode was that it was meant to produce pronouncable ciphertext, which would be cheaper to transmit by telegraph.
This was done by putting all the vowels in the same positions (11 to 16) in every alphabet, and allowing a letter to be enciphered only with a letter at the same position in any of the other 3 alphabets of a disc. Thus, a vowel could only by enciphered by a vowel, and a consonant by a consonant.
Alphabets have a 2-digit number; the first digit (0 to 9) identifying the disc and the second (1 to 4) the alphabet within the disc.
The alphabets for the 10 discs are:
11|MLKJHGFDCBEAYUOIZXWVTSRQPN 12|VTSRQPNMLKYUOIEAJHGFDCBZXW 13|HGFDCBZXWVUOIEAYTSRQPNMLKJ 14|PNMLKJHGFDAYUOIECBZXWVTSRQ
21|JKLMNPQRSTAEIOUYVWXZBCDFGH 22|QRSTVWXZBCUYAEIODFGHJKLMNP 23|NPQRSTVWXZYAEIOUBCDFGHJKLM 24|FGHJKLMNPQEIOUYARSTVWXZBCD
31|GFDCBZXWVTUOIEAYSRQPNMLKJH 32|LKJHGFDCBZEAYUOIXWVTSRQPNM 33|RQPNMLKJHGYUOIEAFDCBZXWVTS 34|WVTSRQPNMLIEAYUOKJHGFDCBZX
41|ZBCDFGHJKLOUYAEIMNPQRSTVWX 42|RSTVWXZBCDUYAEIOFGHJKLMNPQ 43|MNPQRSTVWXAEIOUYZBCDFGHJKL 44|BCDFGHJKLMYAEIOUNPQRSTVWXZ
51|CBZXWVTSRQAYUOIEPNMLKJHGFD 52|XWVTSRQPNMYUOIEALKJHGFDCBZ 53|FDCBZXWVTSEAYUOIRQPNMLKJHG 54|TSRQPNMLKJIEAYUOHGFDCBZXWV
61|STVWXZBCDFUYAEIOGHJKLMNPQR 62|LMNPQRSTVWOUYAEIXZBCDFGHJK 63|XZBCDFGHJKEIOUYALMNPQRSTVW 64|WXZBCDFGHJIOUYAEKLMNPQRSTV
71|ZXWVTSRQPNIEAYUOMLKJHGFDCB 72|NMLKJHGFDCUOIEAYBZXWVTSRQP 73|JHGFDCBZXWYUOIEAVTSRQPNMLK 74|DCBZXWVTSROIEAYUQPNMLKJHGF
81|GHJKLMNPQREIOUYASTVWXZBCDF 82|DFGHJKLMNPOUYAEIQRSTVWXZBC 83|KLMNPQRSTVIOUYAEWXZBCDFGHJ 84|PQRSTVWXZBAEIOUYCDFGHJKLMN
91|QPNMLKJHGFOIEAYUDCBZXWVTSR 92|BZXWVTSRQPUOIEAYNMLKJHGFDC 93|SRQPNMLKJHIEAYUOGFDCBZXWVT 94|KJHGFDCBZXEAYUOIWVTSRQPNML
01|HJKLMNPQRSOUYAEITVWXZBCDFG 02|VWXZBCDFGHEIOUAYJKLMNPQRST 03|CDFGHJKLMNUYAEIOPQRSTVWXZB 04|TVWXZBCDFGAEIOUYHJKLMNPQRS
They are all built using either the normal or the reversed alphabet (vowels removed),within which vowels —grouped in normal or reversed order— are inserted at position 11.
Cryptology
This device shows significant cryptographic weaknesses.
- No letter is at the same position in differents alphabets on a given disc, so no letter is ever enciphered by itself. This allows cryptanalysts the use of cribs, or guessed plaintext.
- This device aims to produce pronounceable text by encrypting a consonant by a consonant and a vowel by a vowel. Practically, this means that for a given ciphertext vowel the only possible plaintext equivalents are the other 5 vowels. The same is true for consonants, which have only 19 possible plaintext equivalents.
- For the same reason, patterns of words (e.g. C-C-V-V-C) can also appear and be a great help to the cryptanalyst.
- If the same key is used for a message longer than 10 letters, the short periodicity of the alphabets can be exploited.
Keyspace
The keyspace for a 10-letter text is:
10! (order of the discs) x 410 (choice of the alphabet, for each disc) x 4 (choice of the plaintext register bar) x 3 (choice of the ciphertext register bar) = 45,660,871,065,600
This is a good example showing that the size of a keyspace does not always reflect the security of a system.


